#
Why Malware Analysis Goes Beyond Sandboxes
Hi everyone!
This is a short post to share a thought I had while working on a malware sample: Should we rely only on sandboxes?, I started thinking about this because the malware I was analyzing wasn’t detected by sandbox environments. Here I won’t be including the in-depth analysis of reversing golang binaries, we can explore it in a future post.
#
The context
I was analyzing a Linux-based GoLang binary that was designed to provide a password. Since we had sandbox environments, we simply uploaded it to see if it was safe or not.
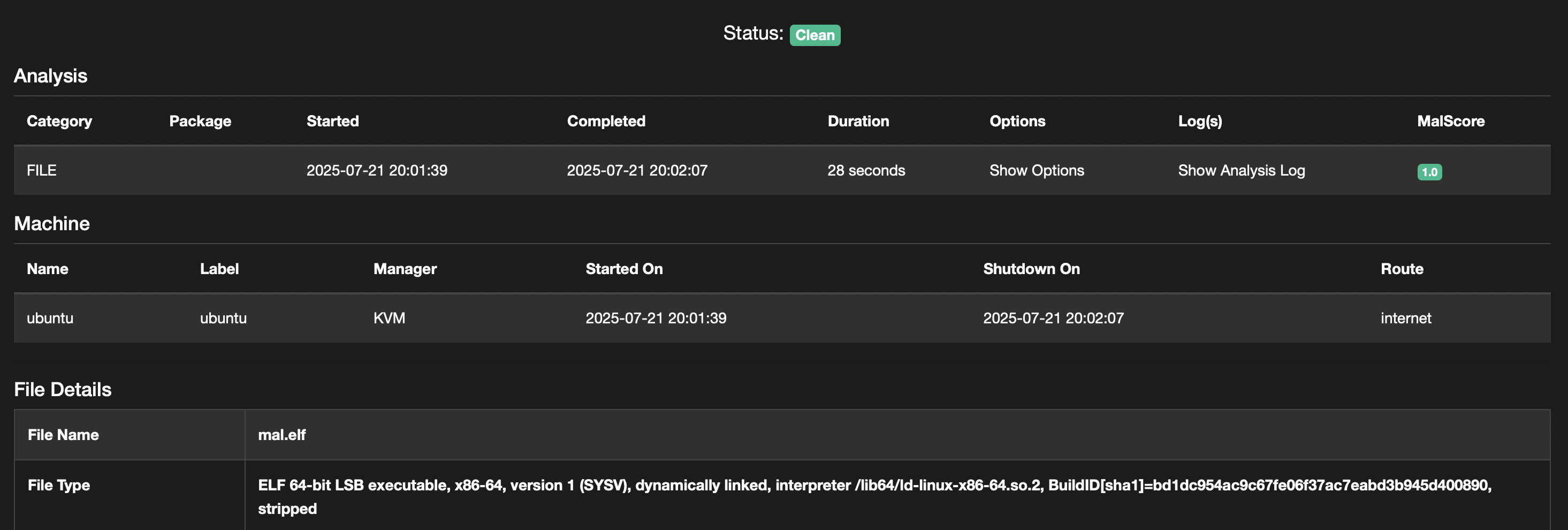
The results from CAPE Sandbox were clean (though it was a simple CAPE setup and required some further tuning). However, when I uploaded this binary to an enterprise EDR sandbox, the results were also same (treated as not suspicious), which was interesting and weird at the same time. So I was curious about this behaviour and tried manual analysis.
Just as we use sandboxes to collect IOCs, malware developers can also gather information about sandbox environments to further improve their anti-VM and anti-sandbox techniques.
#
Role of Reverse Engineering
This is where reverse engineering comes into play. To start with, we don’t need to be an “ultra pro” to figure out whether a sample missed by sandbox is actually malicious.
In our case, this particular sample was stripped but not obfuscated. Just opening it in IDA and debugging it with radare2 gave a clear picture of how the sample works. Even if it had been obfuscated, we could still have identified the malicious signs.
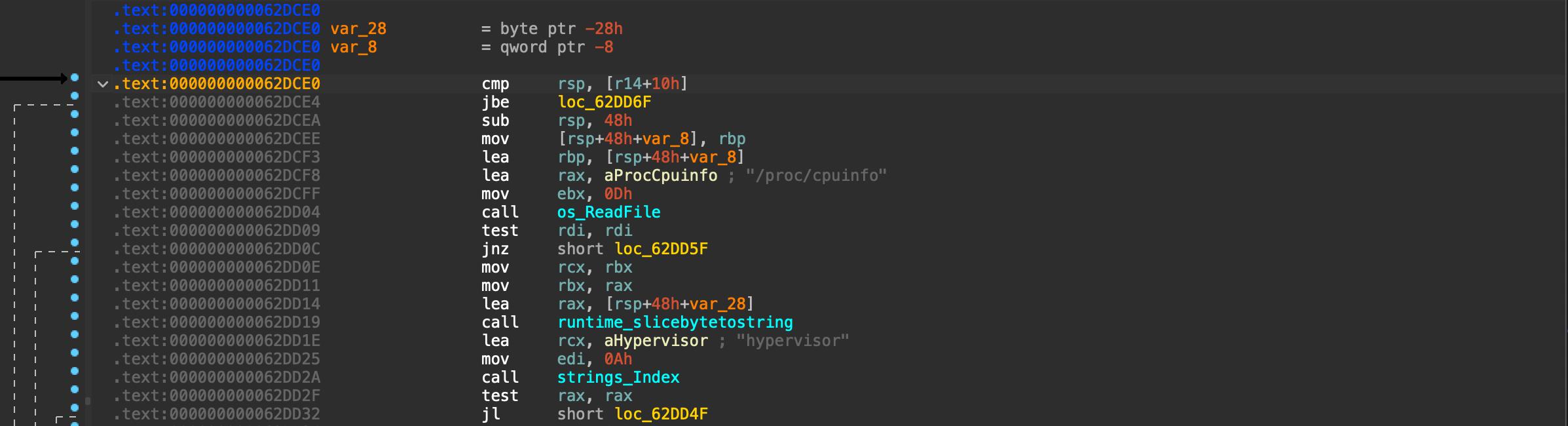
During the dynamic analysis, I found some urls from the sample which was not given by the sandbox environments.
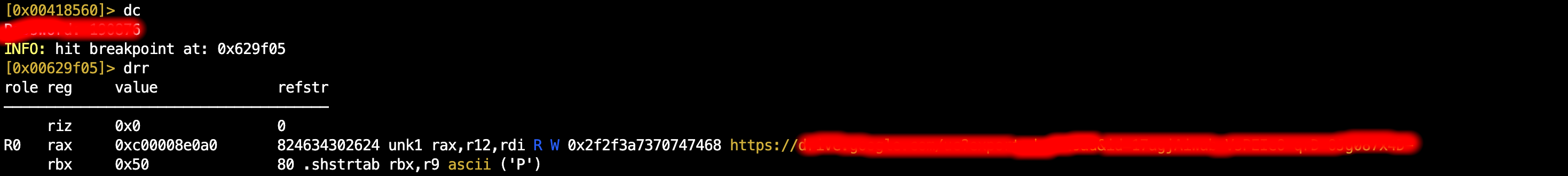
Apparently, there were some authentication mechanisms for the URL that were revoked. As a result, the execution wasn't completed, which maybe a reason for EDR sandbox to not detect anything or simply got exited due to Anti-VM techniques. However, the sandbox still failed to extract the URLs.
In the end, the malware sample was attempting to download files from a URL and execute them, effectively acting as a dropper.
Thanks to reverse engineering, I was able to extract more IOCs and a better understanding of how each functions in the sample works. So, in addition to using sandboxes, we should also perform reverse engineering whenever needed to verify the results.
Sandbox analysis takes an average of 5 minutes to complete. Meanwhile, performing a quick review of the binary using static analysis tools would be very beneficial. In case the sandbox misses the binary, we would still have an idea of what could have gone wrong.
#
Where to learn Reverse Engineering
Starting with programming fundamentals and basic assembly instructions will give you a great head start on the path to reverse engineering. And always remember one thing : learn by doing.
Here are some of my favourite learning sources :-
Crackme Challenges
Github - Awesome Reversing
Youtube - OALabs
Youtube - Dr Josh Stroschein
Youtube - pwn.college
